What is Threat Hunting?
Threat hunting is the proactive process of detecting and investigating abnormal activity on devices and endpoints that may be signs of compromise, intrusion, or ex-filtration of data. This method of defense contrasts with those used by other security solutions like firewalls and security information and event management (SIEM) solutions. These solutions typically complete investigations after a security event has been detected or a breach has occurred. With the ever-evolving cybersecurity landscape, having a proactive cyber threat hunting process is particularly critical to ensure organizational protection.
Why threat hunting is important
Threat hunting is important because sophisticated threats can get past automated cybersecurity. Although automated security tools and tier 1 and 2 security operations center (SOC) analysts should be able to deal with roughly 80% of threats, you still need to worry about the remaining 20%. The remaining 20% of threats are more likely to include sophisticated threats that can cause significant damage. Given enough time and resources, they will break into any network and avoid detection for up to 280 days on average. Effective threat hunting helps reduce the time from intrusion to discovery, reducing the amount of damage done by attackers.
How threat hunting works
A successful threat hunting program is based on an environment’s data fertility. In other words, an organization must first have an enterprise security system in place, collecting data. The information gathered from it provides valuable clues for threat hunters.
Cyber threat hunters bring a human element to enterprise security, complementing automated systems. They are skilled IT security professionals who search, log, monitor and neutralize threats before they can cause serious problems. Ideally, they’re security analysts from within a company’s IT department who knows its operations well, but sometimes they’re an outside analyst.
The art of threat hunting finds the environment’s unknowns. It goes beyond traditional detection technologies, such as security information and event management (SIEM), endpoint detection and response (EDR) and others. Threat hunters comb through security data. They search for hidden malware or attackers and look for patterns of suspicious activity that a computer might have missed or judged to be resolved but isn’t. They also help patch an enterprise’s security system to prevent that type of cyberattack from recurring.
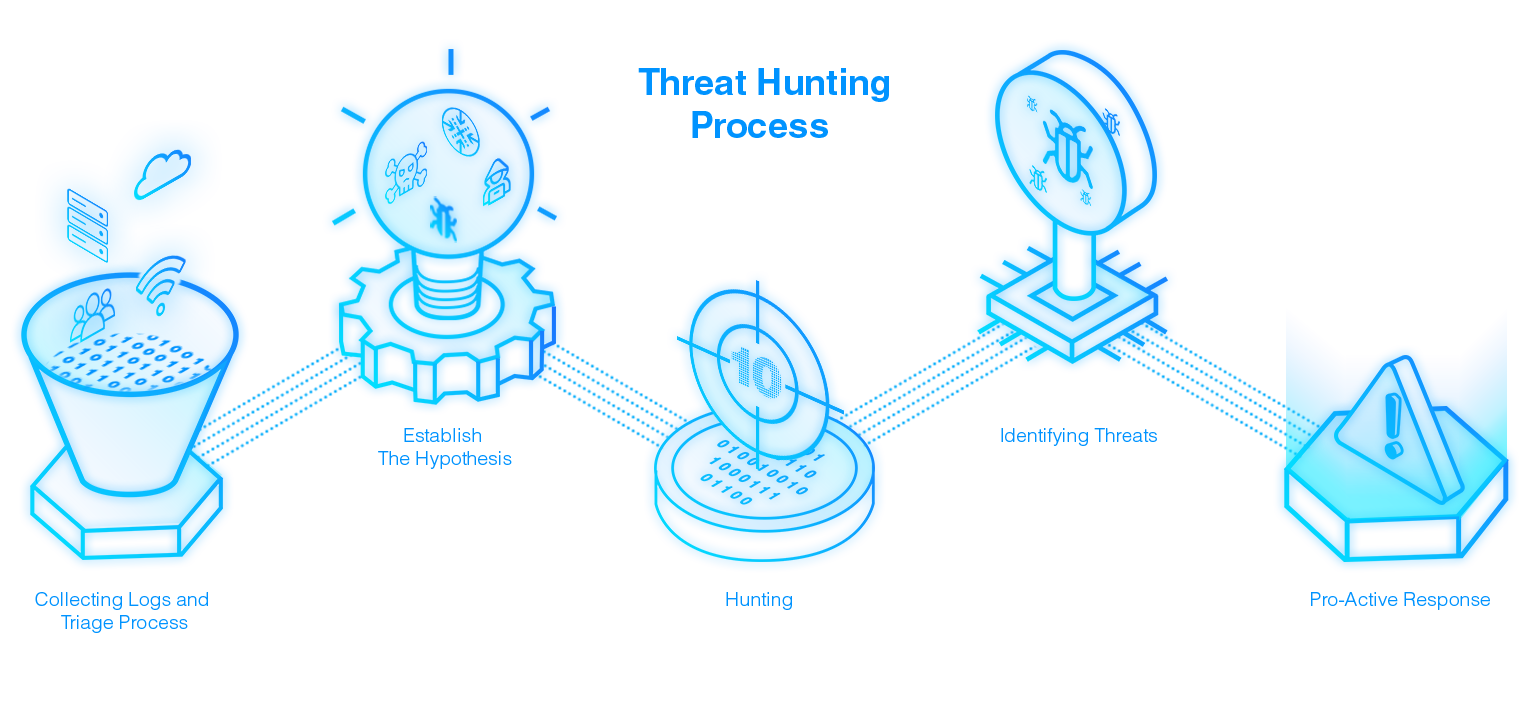
Types of threat hunting
Hunters begin with a hypothesis based on security data or a trigger. The hypothesis or trigger serve as springboards for a more in-depth investigation into potential risks. And these deeper investigations are structured, unstructured and situational hunting.
There are three main investigation styles threat hunters can take, including:
Structured hunting
Structured threat hunting starts with an indicator of attack (IoA) and centers around the tactics, techniques, and procedures (TTPs) of the threat actor. With this type, hunts are often structured around the MITRE ATT@CK Framework, which helps hunters identify a threat actor before damage is done.
Unstructured hunting
Unstructured threat hunting begins with an indicator of compromise (IoC) or trigger. The hunter then looks for patterns in behavior both pre- and post-detection.
Situational or entity driven
Situational threat hunting looks at an enterprise’s individual vulnerabilities, such as those found in a risk assessment. Entity-driven hunting uses external attack data to identify trending TTPs of the latest cyber threats. With this information, hunters can look for specific behaviors within an organization’s own environment.
Threat hunting tools
Hunters conduct their hunts on data from MDR, SIEM, and security analytics technologies. To conduct network-based hunts, they can also make use of additional technologies, such as packer analyzers. However, integrating all necessary sources and tools in an environment is necessary for using SIEM and MDR solutions. Because of this integration, suitable hunting direction can be provided via IoA and IoC indications.
